CVE-2025-4540 - C-Lodop CLodopPrintService unquoted search path
CVE-2025-4540/CNNVD-XXXX (To be confirm)
EN
Info
- Vulnerability Type: Unquoted Service Path Leading to Local Privilege Escalation
- Severity Level: Medium to High
- Vector: Local Windows OS machine
- Attack Complexity: Low
- Privileges Required: Low
- Categories: Local Privilege Escalation
Detail
- Vendor: MTSoftware
- Product: C-Lodop
- Affected Scope: Web Printing Service C-Lodop
- Vulnerable Service: C-Lodop Cloud Printing “No Login” Startup Service
- Affected Version: C-Lodop <= 6.611
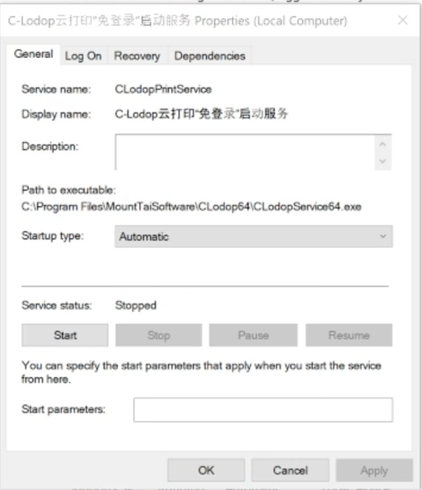
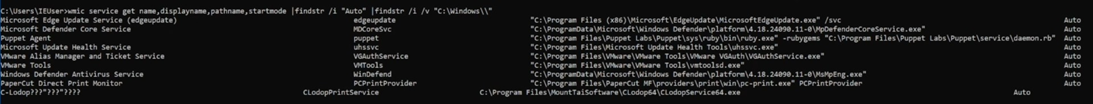
- Description:: An unquoted service path vulnerability in CLodop (<= 6.611) allows a local attacker to escalate privileges via the Program.exe. Since the binary path of the service “CLodopPrintService” is not enclosed in quotes, the Windows Operating system will execute the first instance of the space-separated service path it finds. If the attacker can control write access on C Drive (or other installed Drive), this could lead to local privilege escalation because the CLodopPrintService runs with system privileges.
- Vendor Website: https://www.lodop.net/index.html
- C-Lodop Version Change Log: https://www.lodop.net/c-lodopsteprec.html
1
2Section 6.6.1.3 "修正:增加CLodopPrintService二进制路径引用,封堵诱发本地提权安全漏洞;"
In English: "Fix: Added quotation marks to the CLodopPrintService binary path to mitigate the local privilege escalation vulnerability."
Testing Steps
1. Checking unquoted service path exist
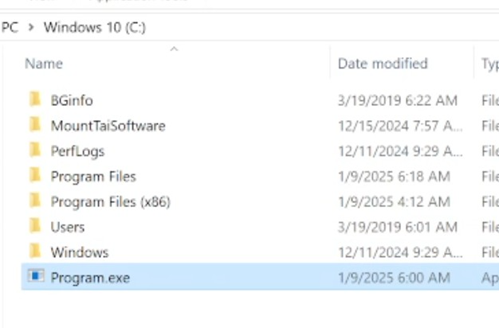
2. Create Program.exe in C Drive directory
3. Restart the CLodopPrintService or reboot the Windows System
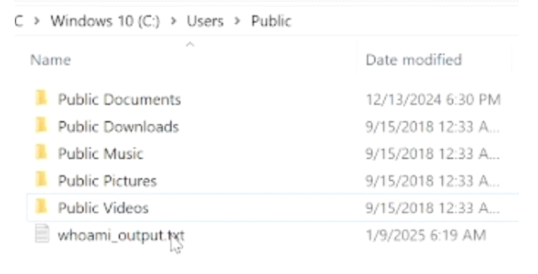
4. The Program.exe will execute whoami /all and output to text file to proof that it is wrote by system privilege
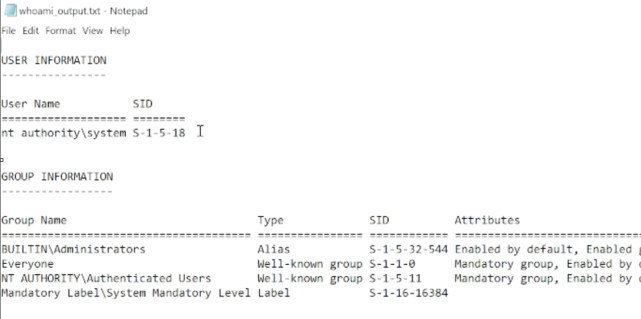
PoC
N.A.
Root Cause
The Service “CLodopPrintService” is not correctly created with quoted best practice.
Official Solution
After testing, it has been confirmed that the issue has been fixed. The vendor has released a patch (6.6.1.3).
Remediation
- Upgrade to C-Lodop version >= 6.613
WorkAround
- Manually modifty the service “CLodopPrintService” to quote the binary path
Timeline
- 2025-01-10 - Submitted a report with PoC to the Lodop team.
- 2025-01-10 - Lodop team confirmed the vulnerability.
- 2025-01-13 - Initial fix confirmed to be effective.
- 2025-01-13 - Lodop team scheduled a fix plan promptly.
- 2025-01-13 - Lodop team confirmed the vulnerability could be disclosed after four weeks.
- 2025-01-13 - Released the patched version 6.6.13.
- 2025-01-13 - Submitted a Vulnerability (CNVD) request to CNVD
- 2025-01-13 - Submitted a CVE request to Mitre CVE portal
- 2025-01-13~ - No response from Mitre CVE
- 2025-03-05 - CNVD requested to update the PoC and Reproduce step (but i have no idea what i need to edit…)
- 2025-04-29 - Submitted a Vulnerability (CVE) request to Vuldb
- 2025-04-29 - Submitted a Vulnerability (CVE) request to Vuldb
- 2025-05-11 - Submitted a Vulnerability (CNNVD) request to CNNVD
- 2025-05-11 - Vuldb Reviewed and Accepted the vulnerability - CVE-2025-4540
Epilogue
Admire for MTSoftware Team in rapid response and patch. Even better than those “Big” vendors…
Mitre CVE portal seems dead (no $)? Seems Vuldb is a better platform now, suggested.
中文
基本資料
- 漏洞類型: 未有引號的服務路徑引致本地提權
- 嚴重程度: 中到高
- 攻擊媒介: Windows 作業系統計算機本機
- 攻擊難度: 低
- 權限需求: 低
- 類別: 本地提權
詳細資料
- 廠商: MTSoftware
- 產品: C-Lodop
- 影響範圍: Web打印服务C-Lodop
- 缺陷服務: C-Lodop云打印“免登录”启动服务
- 涉及版本: C-Lodop <= 6.611
- 簡介: 由於服務”CLodopPrintService”的二進位路徑未包含在引號中,則作業系統將會執行找到的空格分隔的服務路徑的第一個實例。如果攻擊者可以控制在C Drive的寫入,而CLodopPrintService以系統權限執行,即可引致本地提權。
- 廠商網站: https://www.lodop.net/index.html
- C-Lodop 版本記錄: https://www.lodop.net/c-lodopsteprec.html
1
Section 6.6.1.3 "修正:增加CLodopPrintService二进制路径引用,封堵诱发本地提权安全漏洞;"
測試步驟
1. 檢查服務路徑沒有雙引號


2. 在C Drive 寫入Program.exe

3. 重啟CLodopPrintService, 但重啟Windows系統有一樣效果
4. Program.exe會執行whoami /all指令及將結果寫入文件去證明提權成功


PoC
N.A.
根本原因
由於服務”CLodopPrintService”路徑未按照對於引號的Windows服務最佳實踐去正確建立。
官方解決方案
廠商發布已修復版本(6.6.13)
補救措施
- C-Lodop 升級至 6.6.13 或更新版本
變通辦法
- 手動修改服務”CLodop Print Service”路徑, 添加雙引號
時間線
- 2025-01-10 - 向 Lodop 團隊提交了一份帶有 PoC 的報告。
- 2025-01-10 - Lodop 團隊確認了該漏洞。
- 2025-01-13 - 初步修復確認有效。
- 2025-01-13 - Lodop 團隊及時制定了修復計劃。
- 2025-01-13 - Lodop 團隊確認漏洞可在四週後揭露。
- 2025-01-13 - 發布修補版本 6.6.13。
- 2025-01-13 - 向 CNVD 提交了漏洞 (CNVD) 請求
- 2025-01-13 - 向 Mitre CVE 網站提交了 CVE 請求
- 2025-01-13~ - Mitre CVE 沒有回應
- 2025-03-05 - CNVD 請求更新 PoC 和重現步驟(但我不知道需要編輯什麼…)
- 2025-04-29 - 向 Vuldb 提交了漏洞 (CVE) 請求
- 2025-04-29 - 向 Vuldb 提交了漏洞 (CVE) 請求
- 2025-05-11 - 向 CNNVD 提交了漏洞 (CNNVD) 請求
- 2025-05-11 - Vuldb 審核並接受了漏洞 - CVE-2025-4540
後記
欣賞 MTSoftware 團隊反應之迅速, 比某啲”大企業”做得更快更好。
Mitre CVE 無錢冚旗?建議用Vuldb, 都幾快有result。
All articles on this blog are licensed under CC BY-NC-SA 4.0 unless otherwise stated.
