Hackthebox Sherlocks Takedown
Hackthebox Sherlocks - Takedown
Info
- Level: Easy
- Category: SOC
Briefly review files
Takedown.pcap- SMB traffic
- HTTP traffic
Tasks
Task 1: From what domain is the VBS script downloaded
search keyword vbs in wireshark.
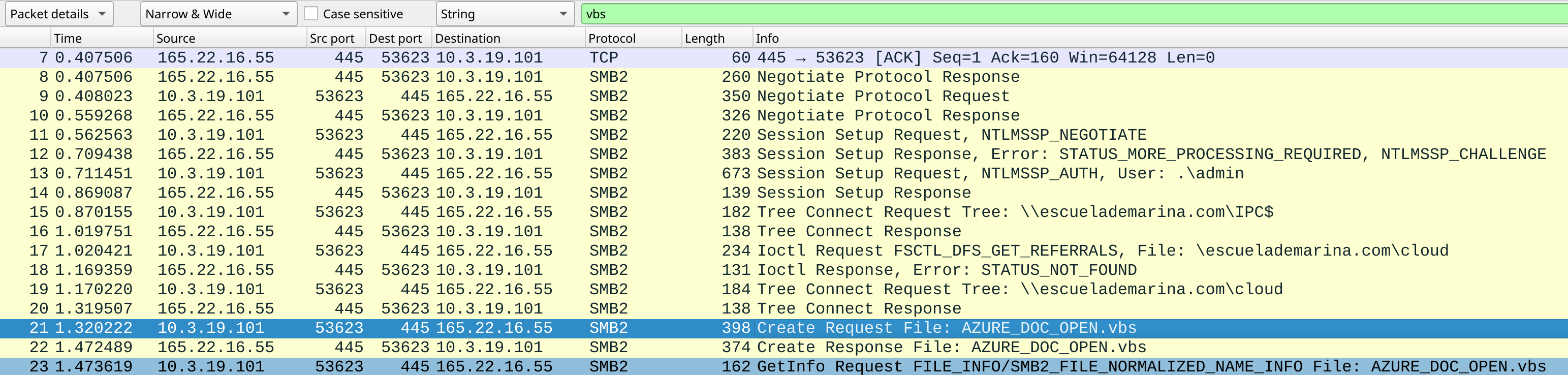
Click Find a packet (magnifier icon) -> Packet Detail -> Narrow and Wide -> String -> vbs
Answer: escuelademarina.com
Task 2: What was the IP address associated with the domain in question #1 used for this attack?
Answer: 165.22.16.55
Task 3: What is the filename of the VBS script used for initial access?
Answer: AZURE_DOC_OPEN.vbs
Task 4: What was the URL used to get a PowerShell script?
File -> export object -> SMB -> Save all
File: %5cAZURE_DOC_OPEN(1).vbs
1 | tjfzjfht = "powershell" |
vbs call powershell to download file.
Answer: badbutperfect.com/nrwncpwo
Task 5: What likely legit binary was downloaded to the victim machine?
File -> export object -> HTTP -> search nrwncpwo -> Save
Content:
1 | ni 'C:/rimz' -Type Directory -Force; |
powershell script download the legit executables and run the malicious script, lolbas technique.
Answer: AutoHotkey.exe
Task 6: From what URL was the malware used with the binary from question #5 downloaded?
Answer: http://badbutperfect.com/jvtobaqj
Task 7: What filename was the malware from question #6 given on disk?
Answer: script.ahk
Task 8: What is the TLSH of the malware?
File -> export object -> HTTP -> search jvtobaqj -> Save
Emmm, the file contains a lot of rubbish content…
But we need the TLSH…
1 | sha256sum jvtobaqj |
From virustotal, search 5aac7d31149048763e688878c3910ae4881826db80e078754f5d08f2c1f39572 to get the TLSH hash from Detail -> basic properties.
Answer: T15E430A36DBC5202AD8E3074270096562FE7DC0215B4B32659C9EF16835CF6FF9B6A1B8
filter out the rubbish content:
Using vscode regex search and replace \/\*.*?(.|[\n])*?\*\/ to replace those rubbish content with empty.
1 | #NoTrayIcon |
Seems just common shellcode calling.
Task 9: What is the name given to this malware? Use the name used by McAfee, Ikarus, and alejandro.sanchez.
Check Virustotal -> Associations
Answer: DarkGate
Task 10: What is the user-agent string of the infected machine?
Check HTTP request traffics,
Answer: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/118.0.0.0 Safari/537.36
Task 10: To what IP does the RAT from the previous question connect?
Answer: 103.124.105.78
