Hackthebox Sherlocks Compromised
Hackthebox Sherlocks - Compromised
Info
- Level: Easy
- Category: SOC
Briefly review files
capture.pcap- SMB traffic
- HTTP traffic
- TLS traffic
- DNS traffic
Tasks
Task 1: What is the IP address used for initial access?
Quickly filter the http protocol traffic, there are few packets only.
and first request and response GET /9GQ5A8/6ctf5JL HTTP/1.1 seems interesting.
Although it shows that it is image/gif, data is MZ header which means that it should be Windows executables.
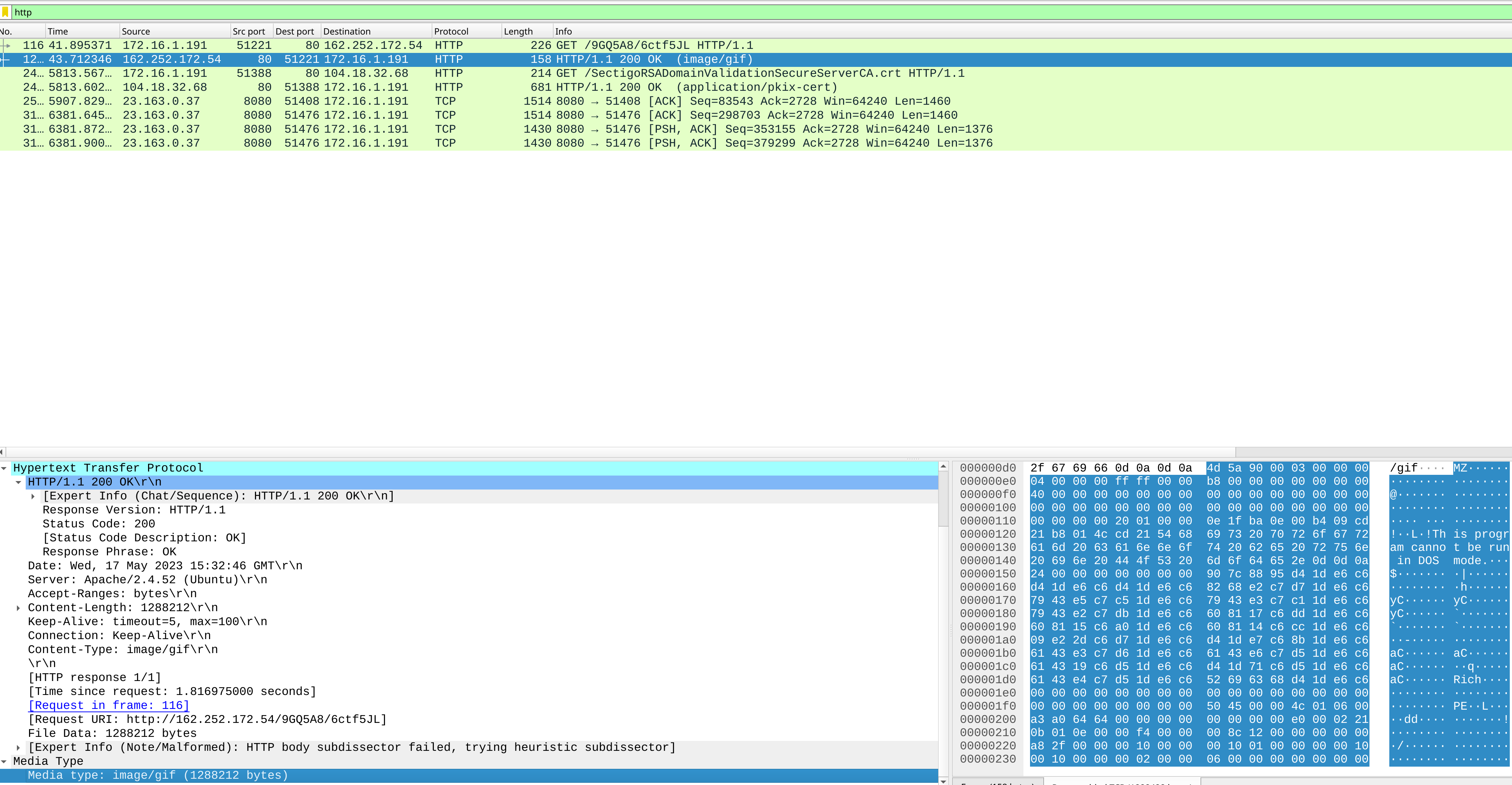
Answer: 162.252.172.54
Task 2: What is the SHA256 hash of the malware?
Export the HTTP object.
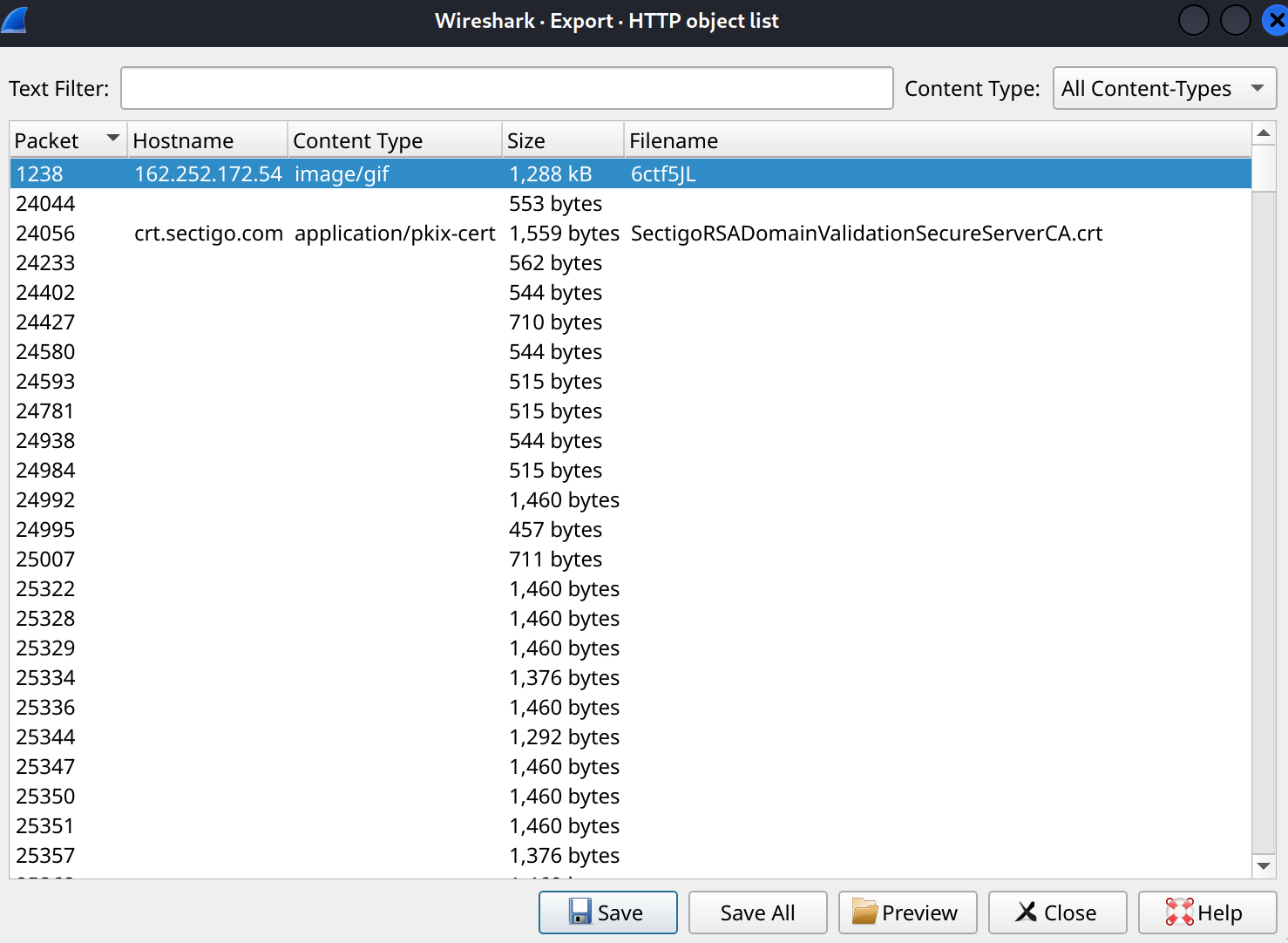
1 | sha256sum 6ctf5JL |
Answer: 9b8ffdc8ba2b2caa485cca56a82b2dcbd251f65fb30bc88f0ac3da6704e4d3c6
Task 3: What is the Family label of the malware?
Search in virustotal associations:
https://www.virustotal.com/gui/file/9b8ffdc8ba2b2caa485cca56a82b2dcbd251f65fb30bc88f0ac3da6704e4d3c6/associations
Answer: Pikabot
Task 4: When was the malware first seen in the wild (UTC)?
Just virustotal detail record:
https://www.virustotal.com/gui/file/9b8ffdc8ba2b2caa485cca56a82b2dcbd251f65fb30bc88f0ac3da6704e4d3c6/details
Answer: 2023-05-19 14:01:21
Task 5: The malware used HTTPS traffic with a self-signed certificate. What are the ports, from smallest to largest?
First of all, filter (ssl||tls) SSL or TLS traffic.
Some Destination ports are not common service ports but i think we need to know the certificate issuer and subject to ensure that it is self-signed or not.
ssl.handshake.type==11 means certificate.
Here is the tshark query:tshark -r capture.pcap -Y "(ssl||tls) && ssl.handshake.type==11" -T fields -e ip.src -e tcp.srcport -e ip.dst -e tcp.dstport -e x509sat.uTF8String -e x509sat.printableString -e tls.handshake.certificate -E separator=, -E header=y
x509sat.uTF8String: extract the issuer data.x509sat.printableString: extract the subject data.tls.handshake.certificate: extract the raw certificate.
The simplest way is checking that issuer == subject.
I found a python script to check the pcap to rearch my objective: https://github.com/89oinotna/tlsCertificateInspector
However, seems because of some library changes, failed to run the script.
Helped with GPT, i wrote a similar script to do the same task.
My Script: https://github.com/0Nightsedge0/Check_SelfSigned_From_Pcap
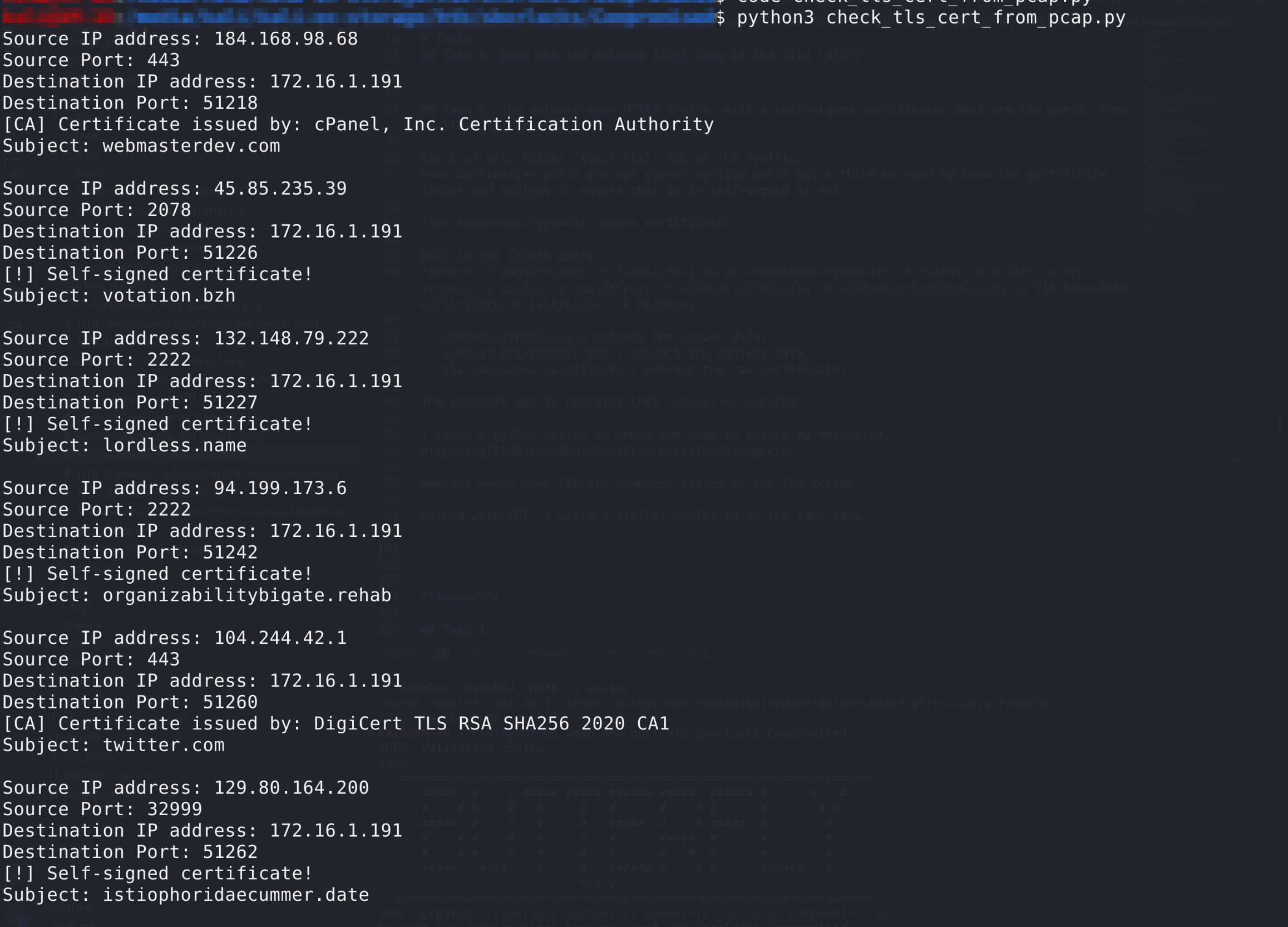
Answer: 2078, 2222, 32999
Task 6: What is the id-at-localityName of the self-signed certificate associated with the first malicious IP?
See my script, extracted this field.
Answer: Pyopneumopericardium
Task 6: What is the notBefore time(UTC) for this self-signed certificate?
See my script, extracted this field.
Answer: 2023-05-14 08:36:52
Task 7: What was the domain used for tunneling?
So suddenly asking for tunnel…
I guess DNS tunnel or SSH tunnel…?
After filter the dns traffic, there are lots of txt dns record with long data response.
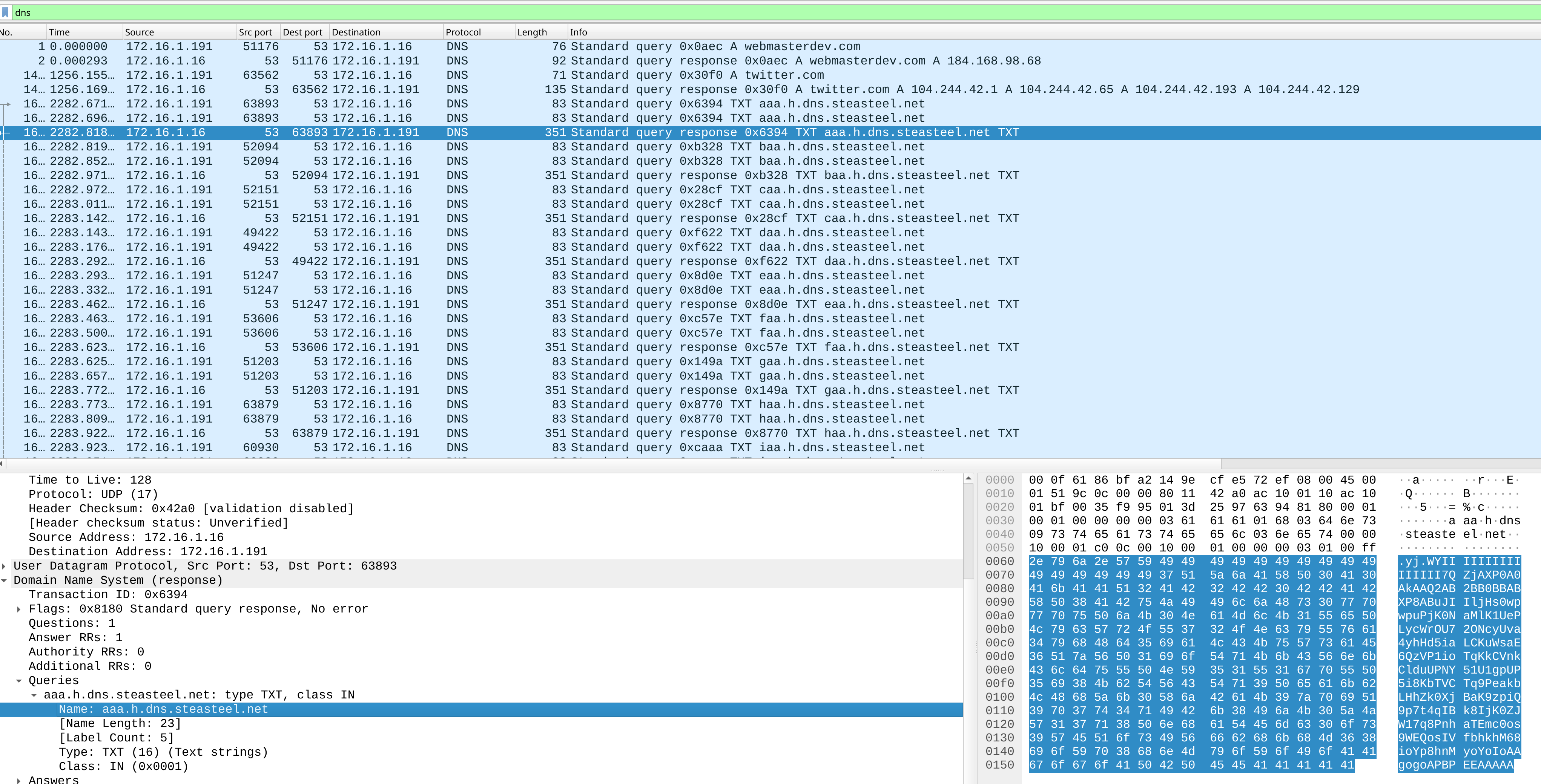
Answer: steasteel.net
