HKCert CTF Forensic - Wheres the APT Attack 3 Guide
HKCert CTF Forensic - Q3: Where’s the APT Attack? APT攻擊在哪裡? Hidden Flag? 隱藏旗?
Info
- Author: Nightsedge
- Categories: forensics
- Hidden Question!
Question Description (zh-HK)
請以第2題繼續。
您是高級網絡安全分析師。
您的經理要求您協助分析Windows內存映像,作為我們目前調查的一部分。
這臺受害機器已經被隔離,Windows內存映像已經被提取供您調查。
預計內存映像將揭示一個包含命令和控制(C2)進程的常見程序,通常被稱為信標 (beacon)。
隱藏旗。如果大神您找到的話請跟在下交流一下IR心法,
Question Description (en)
Please continue from Q2.
You are the Senior Cybersecurity Analyst.
Your Manager is requesting your assistance in analyzing a Windows memory image as a component of our current investigation.
This victim machine has been isolated and the Windows memory image has been extracted for your review.
The memory image is expected to reveal a routine that includes a command and control (C2) process, commonly known as a beacon.
There is a hidden flag! It will be great to contact me if you can find it, you should be very great in IR.
Steps
- Review the C# DLL program from Q2
- Guess the command and control (C2) framework
- Read Didier Stevens’s articles from SANS (Strongly Recommended)
- Decrypt and Parse the beacon file, and get the Cobalt Strike beacon setting profile
Warning
- Real Malware
- Can bypass Anti-Virus Solutions
- Almost no signature? maybe not?
- Not useful: malfind (because no signature), yarascan (or you have your own great Yara signature)
- The author (me) is too lazy to tidy up the write-ups~
Guide
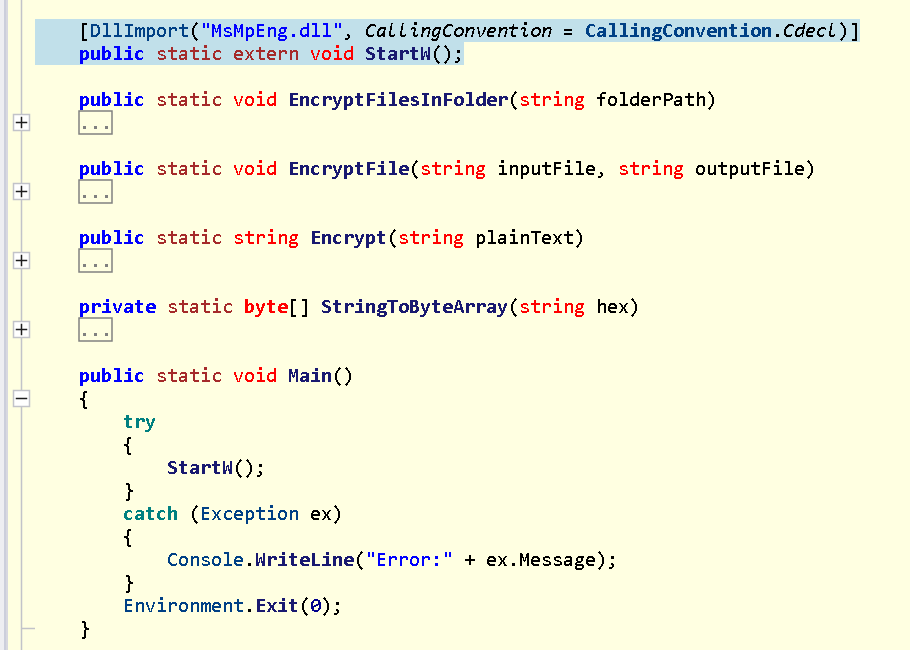
1. Review the C# DLL program from Q2
The mpclient.dll called the MsMpEng.dll function StartW which is common export function from Cobalt Strike DLL stage/stageless beacon.
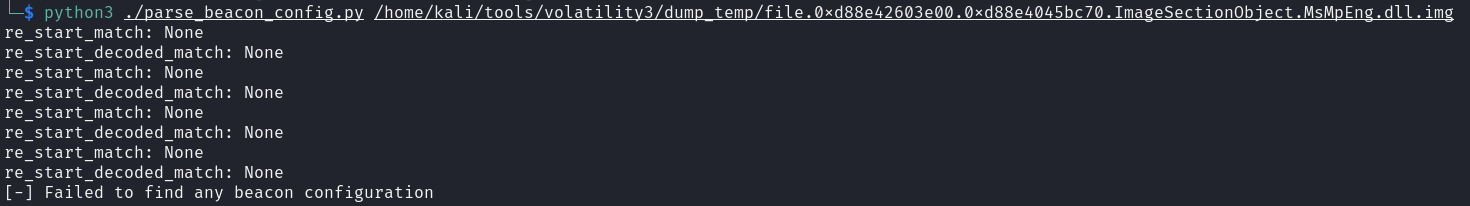
2. Extract profile using Sentinel-One’s CobaltStrikeParser?
Sorry, no matched starting point.
Because the shellcode is encrypted with an unknown XOR key. =]
1 | python3 ./parse_beacon_config.py file.0xd88e42603e00.0xd88e4045bc70.ImageSectionObject.MsMpEng.dll.img |
3. Analysis of an Encoded Cobalt Strike Beacon by Didier Stevens
This very great article by Didier Stevens:
https://isc.sans.edu/diary/Analysis+of+an+Encoded+Cobalt+Strike+Beacon/29014
Strongly recommended to read the article again!
Follow this article’s ideas and steps to continue your analysis.
XOR known plaintext attacks!
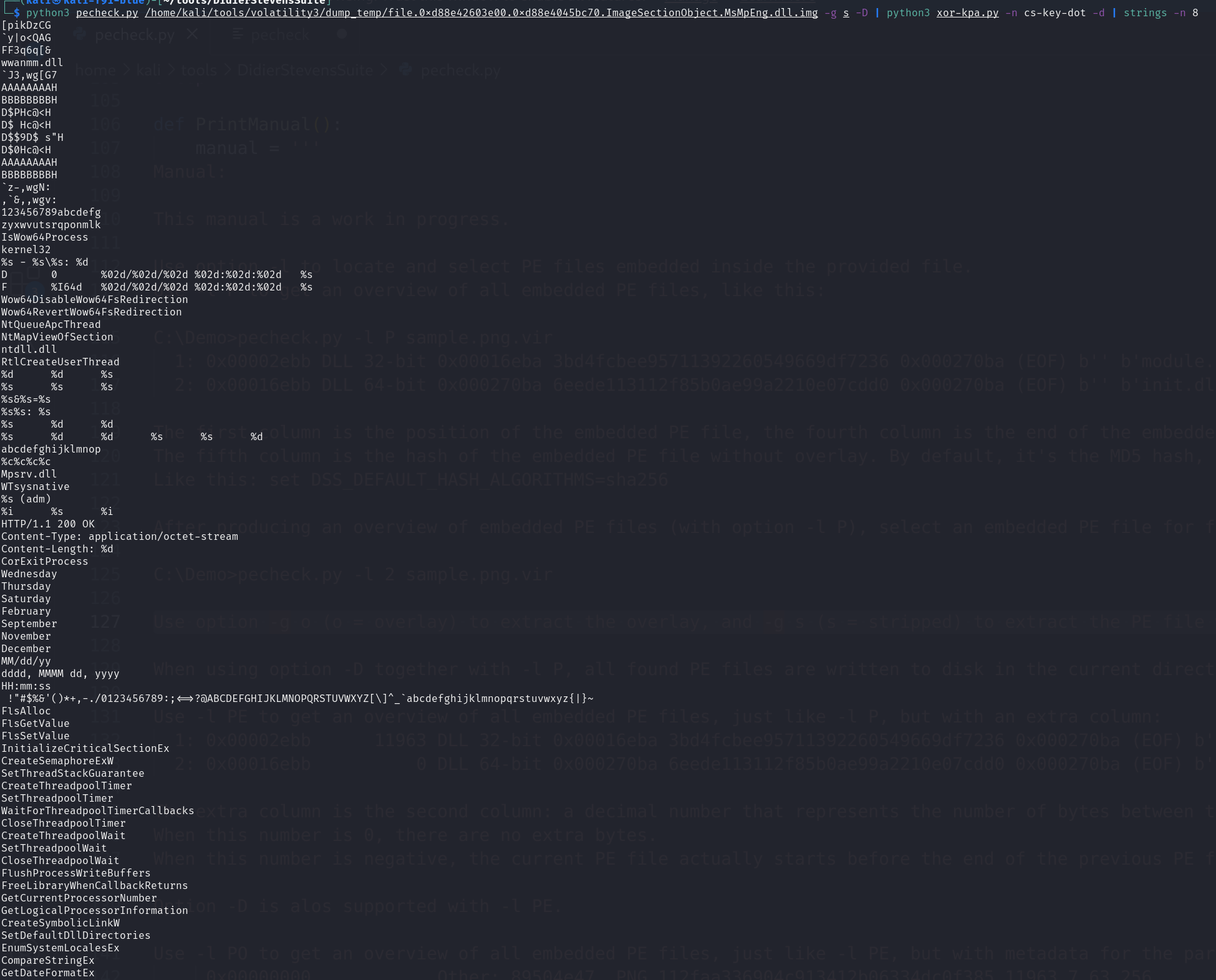
Use option -g o (o = overlay) to extract the overlay, and -g s (s = stripped) to extract the PE file without overlay.
1 | python3 pecheck.py file.0xd88e42603e00.0xd88e4045bc70.ImageSectionObject.MsMpEng.dll.img -g s -D | python3 xor-kpa.py -n cs-key-dot |
Now you can find the meanful strings, some windows API calls and file names.
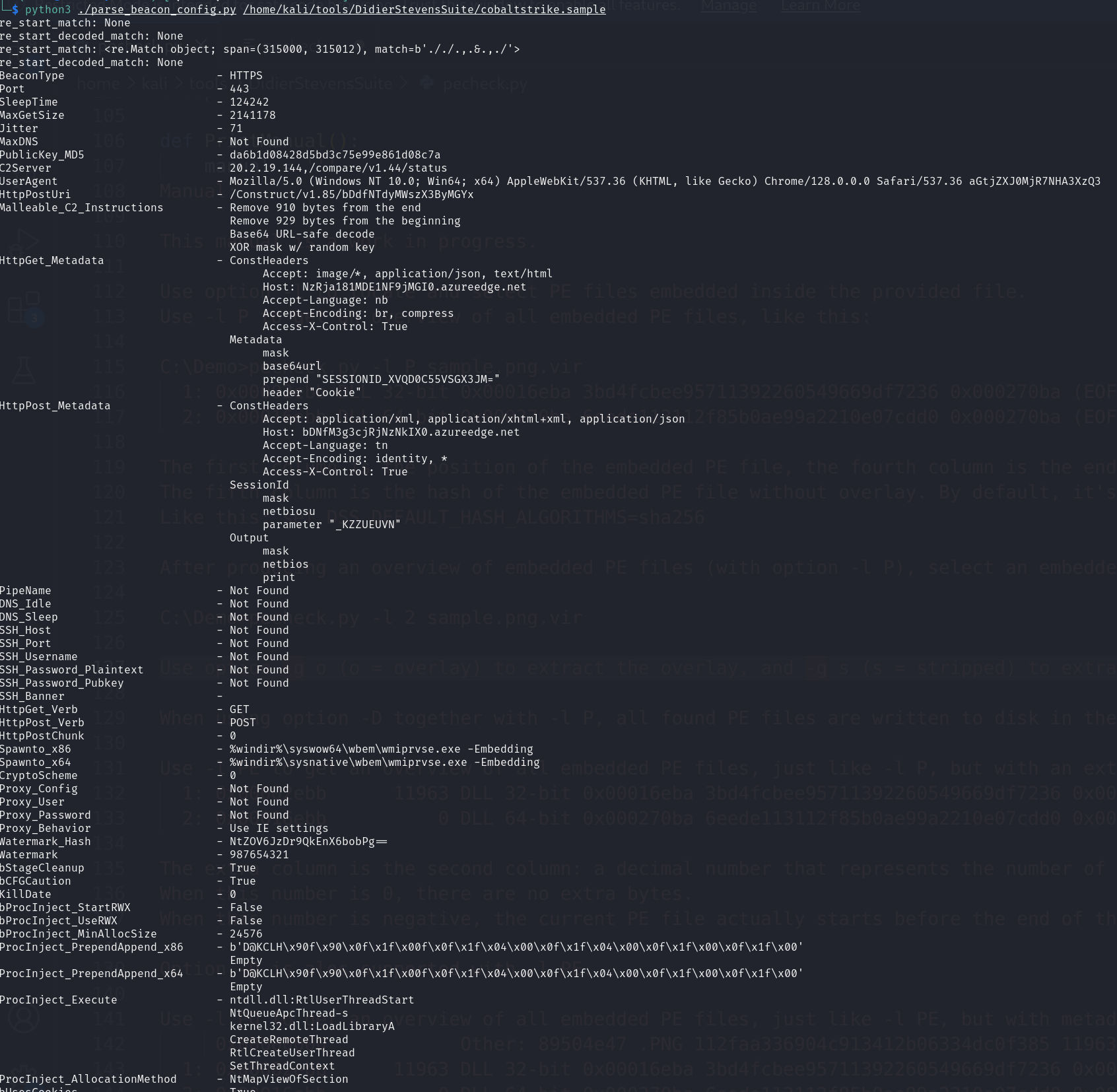
4. Extract the Cobalt Strike profile and pretty print the beacon profile
1 | python3 pecheck.py file.0xd88e42603e00.0xd88e4045bc70.ImageSectionObject.MsMpEng.dll.img -g s -D | python3 xor-kpa.py -n cs-key-dot -d > cobaltstrike.sample |
5 Flag from profile
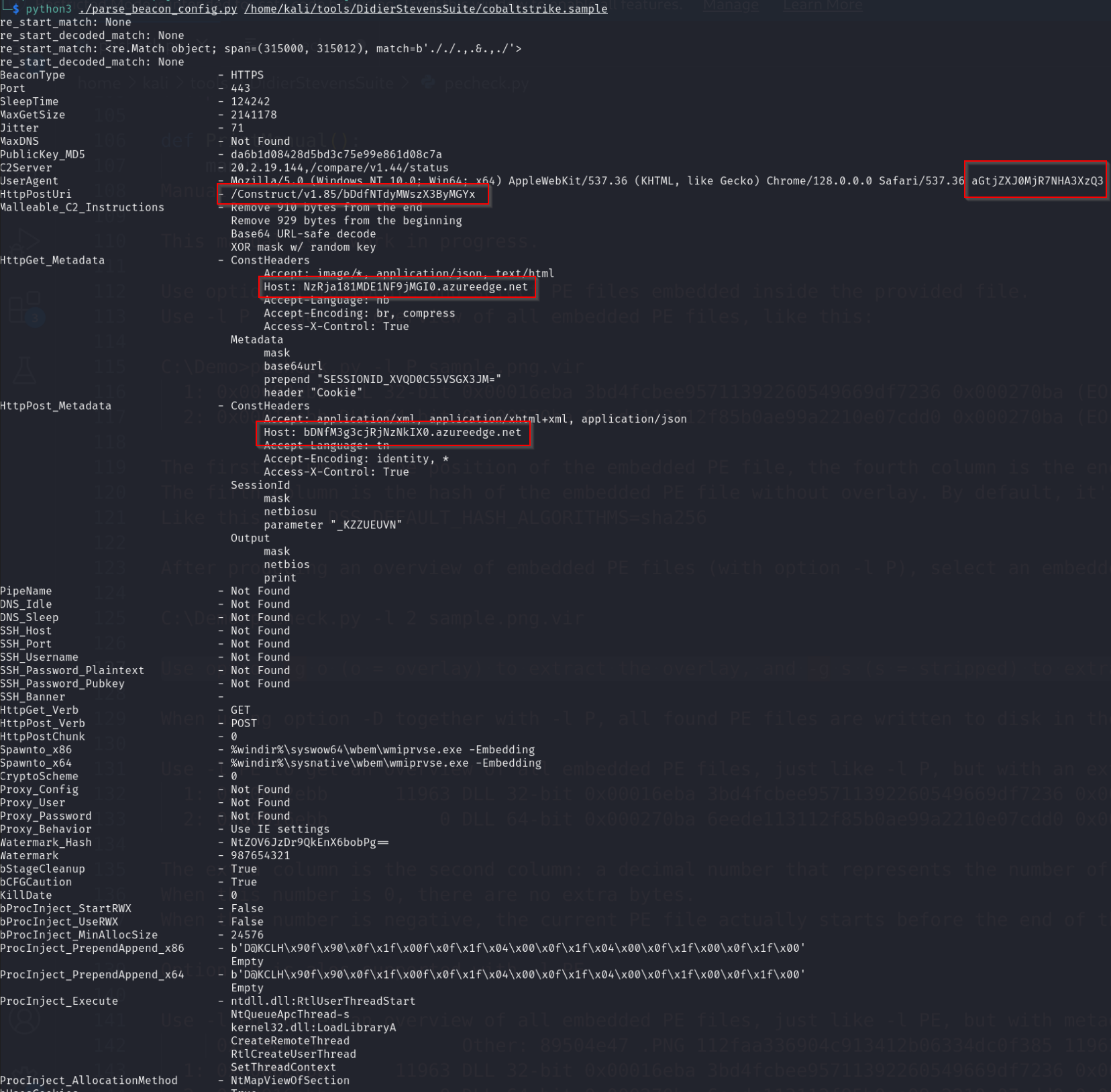
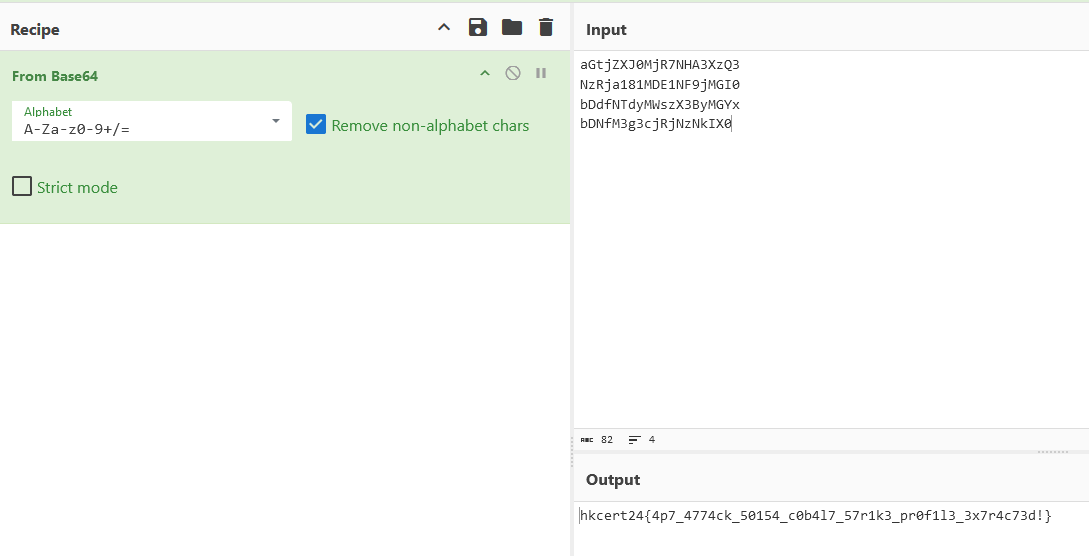
Flag
1 | hkcert24{4p7_4774ck_50154_c0b4l7_57r1k3_pr0f1l3_3x7r4c73d!} |
