HKCert CTF Forensic - Wheres the APT Attack 2 Guide
HKCert CTF Forensic - Q2: Where’s the APT Attack? APT攻擊在哪裡? Suspicious process 可疑進程
Info
- Author: Nightsedge
- Categories: forensics
Question Description (zh-HK)
請以第1題繼續。
您是高級網絡安全分析師。
您的經理要求您協助分析Windows內存映像,作為我們目前調查的一部分。
這臺受害機器已經被隔離,Windows內存映像已經被提取供您調查。
預計內存映像將揭示一個包含命令和控制(C2)進程的常見程序,通常被稱為信標 (beacon)。
請找出信標進程中的旗。只需要一點逆向技巧吧?
Question Description (en)
Please continue from Q1.
You are the Senior Cybersecurity Analyst.
Your Manager is requesting your assistance in analyzing a Windows memory image as a component of our current investigation.
This victim machine has been isolated and the Windows memory image has been extracted for your review.
The memory image is expected to reveal a routine that includes a command and control (C2) process, commonly known as a beacon.
Please find the flag from the beacon process. Just need a bit of Reverse engineering technique?
Steps
- Open and analyze the memory image by using Volatility3 and MemProcFS
- Identify the interesting persistence
- Identify the malicious process
- Identify the real malicious file and get flag from the process images
Warning
- Real Malware
- Can bypass Anti-Virus Solutions
- Almost no signature? maybe not?
- Not useful: malfind (because no signature), yarascan (or you have your own great Yara signature)
- The author (me) is too lazy to tidy up the write-ups~
Guide
1. Find the persistence via MemProcFS
After you checked a lot, you can find that there are 2 tasks one is Windows Defender Scheduled Scan and another one is Windows Defender Scheduled Scan-1 because of the naming convention from MemProcFS.
From timeline_task.csv, it already showed this abnormal task.
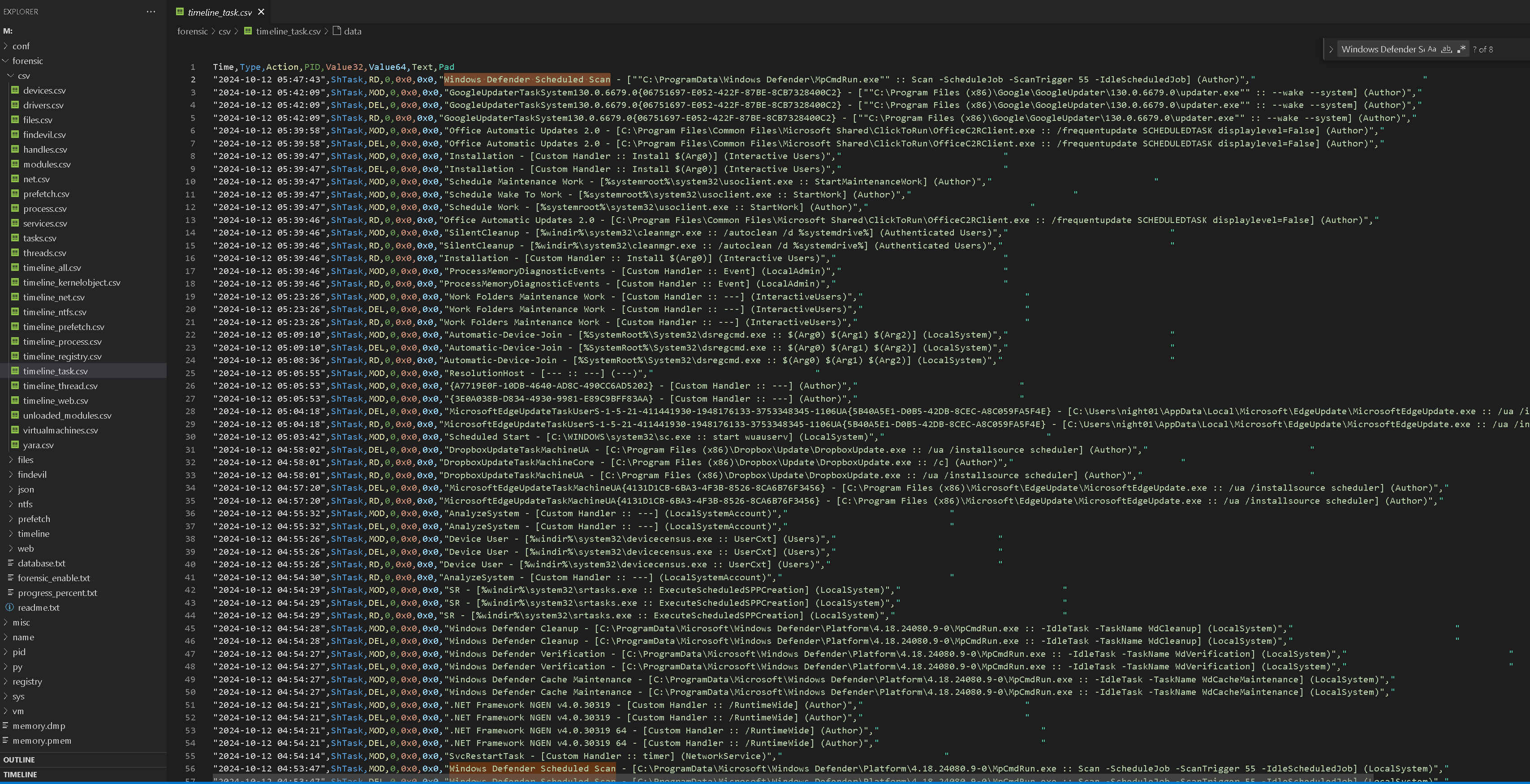
There are 2 scheduled tasks with same name. However,
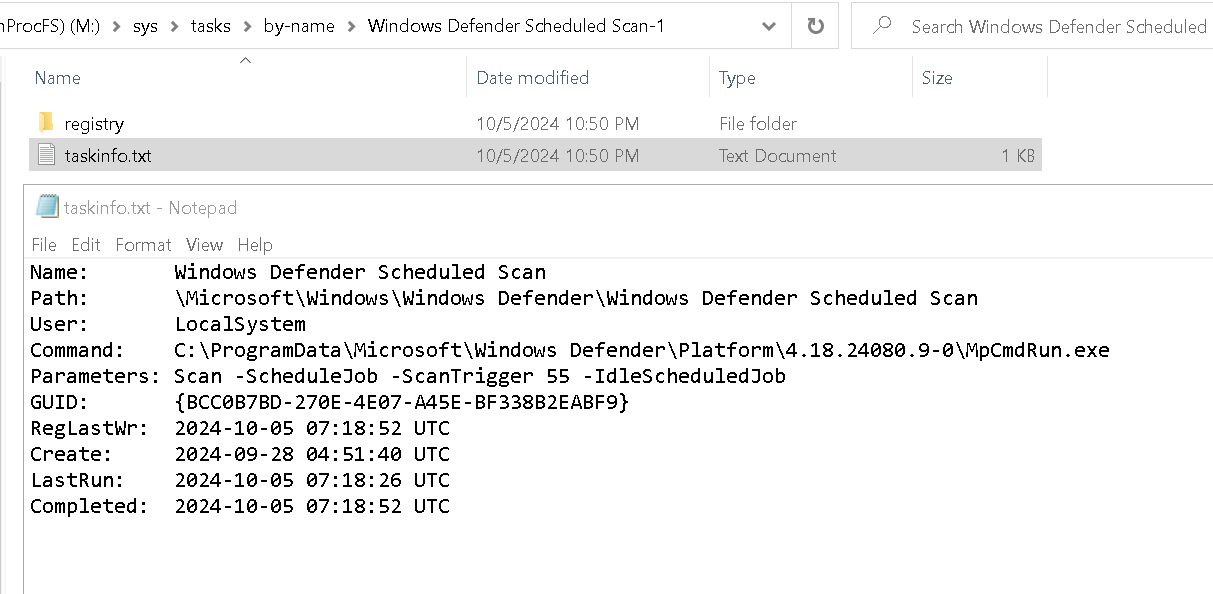
Windows Defender Scheduled Scan-1is created by the system, which is a real and legitimate task.
Windows Defender Scheduled Scanis created byDIGITALHARBOUR\night01, which should not be a legitimate task, possibly persistence with a fake name.
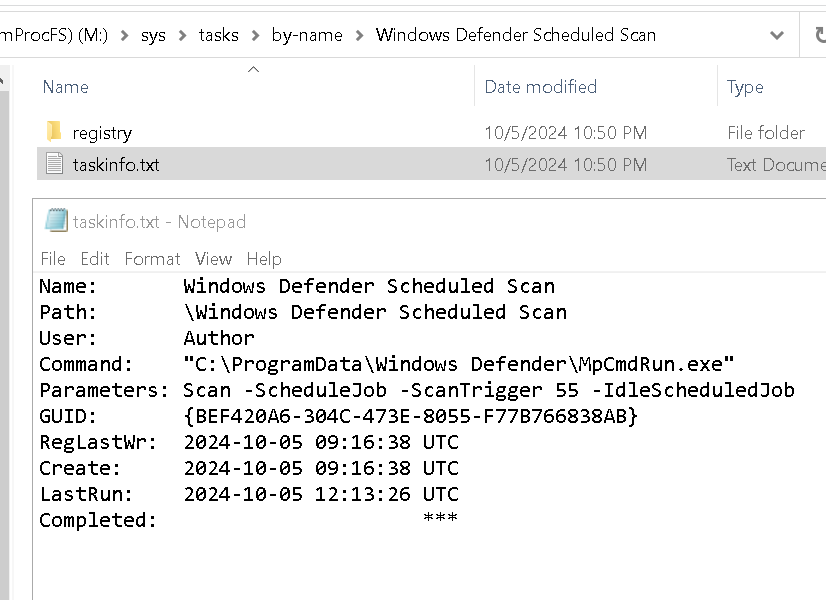
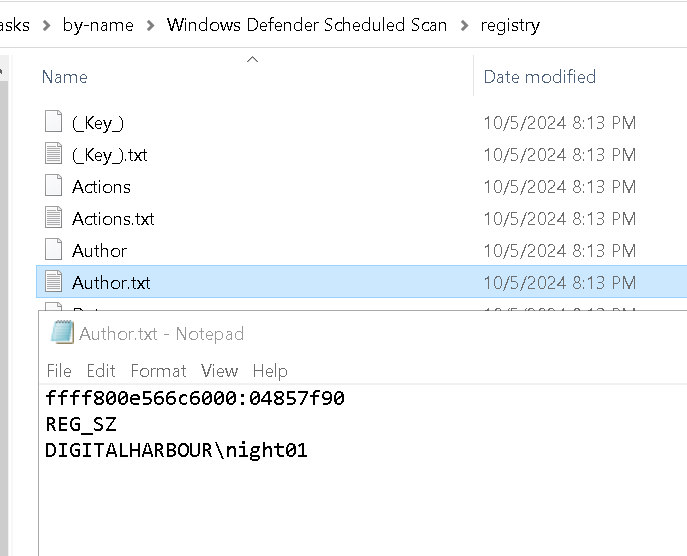
And its action is ProgramData\Windows Defender\MpCmdRun.exe, which seems a bit wired.

Also, the timeline_ntfs.csv from MemProcFS shows that the file creation and the update on this folder ProgramData\Windows Defender\.
2.1 Using netscan function to get all the network connected processes and export as CSV format
1 | vol.py -r csv -f /home/kali/Downloads/hk_oct_apt_attack.mem windows.netscan.NetScan > ./review_records/windows.netscan.NetScan.csv |
Save it as a xlsx excel file and paste records to the new excel sheet.
Although you can search the reputation of the ForeginAddr IP addresses Threat Intelligence (TI), you know those results are still unrated or safe.
2.2 Using pstree function to get all the network activities processes and export as CSV format
1 | vol.py -r csv -f /home/kali/Downloads/hk_oct_apt_attack.mem windows.pstree.PsTree > ./review_records/windows.pstree.PsTree.csv |
And copy the result to the netscan excel with a new sheet.
2.3 Filter out network activities process by looking up the netscan excel results
=INDEX(windows.netscan.NetScan!F:F, MATCH(windows.pstree.PsTree!$B2, windows.netscan.NetScan!$I:$I,0))
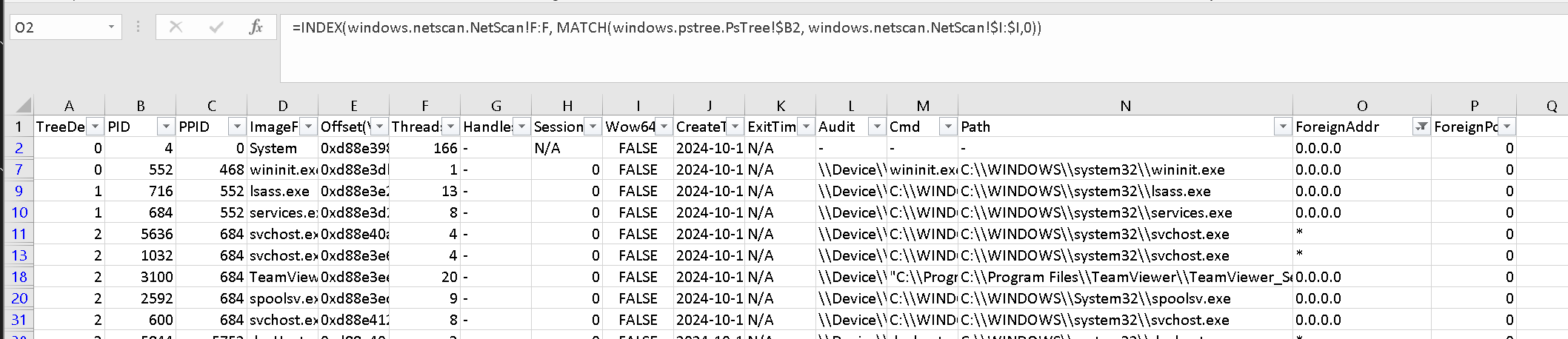
Filter out the N.A. values.
Suggested to collect those PIDs and listing them for further investigation.
2.4 Short Sumup the findings
As an experienced blue team or IR member, you will find that the MpCmdRun.exe file path is not an expected path!
MpCmdRun.exe (PID: 10344) is the Microsoft Defender Anti-Virus Software CMD toolkit. (legit application)
The correct path is \ProgramData\Microsoft\Windows Defender\Platform\<antimalware platform version>\MpCmdRun.exe from Microsoft Document.C:\\ProgramData\\Windows Defender\\MpCmdRun.exe is not correct.
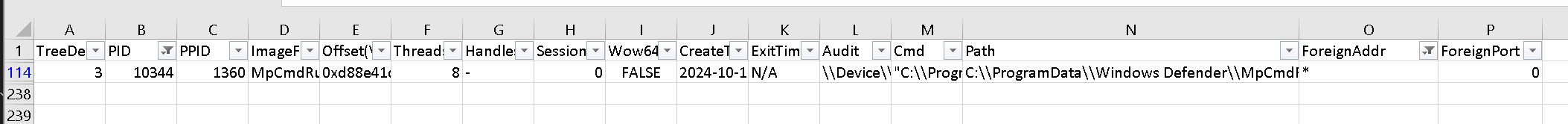
Therefore, it is believed that it is not an expected process from an abnormal scheduled task.
3. Find the real malicious file
3.1 Dump the possible process executable files
1 | vol.py -f /home/kali/Downloads/hk_oct_apt_attack.mem -o ./dump_temp/ windows.dumpfiles.DumpFiles --pid 10344 |
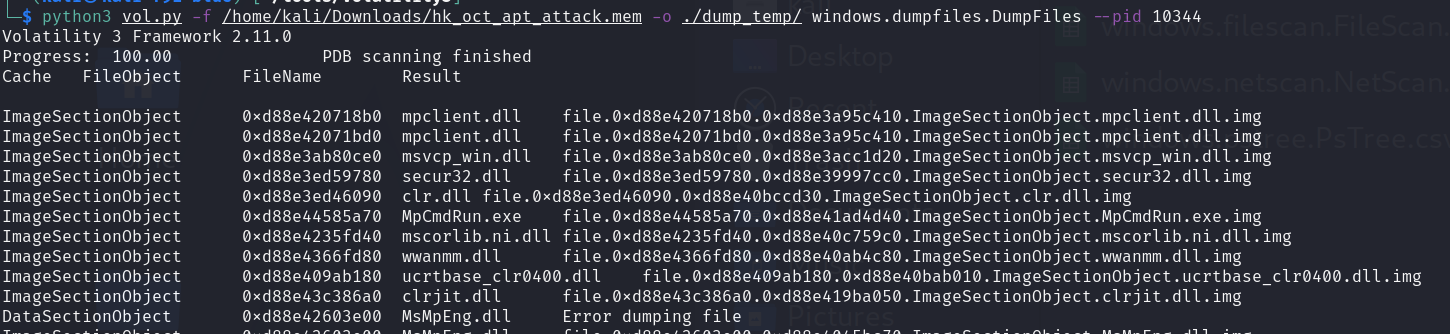
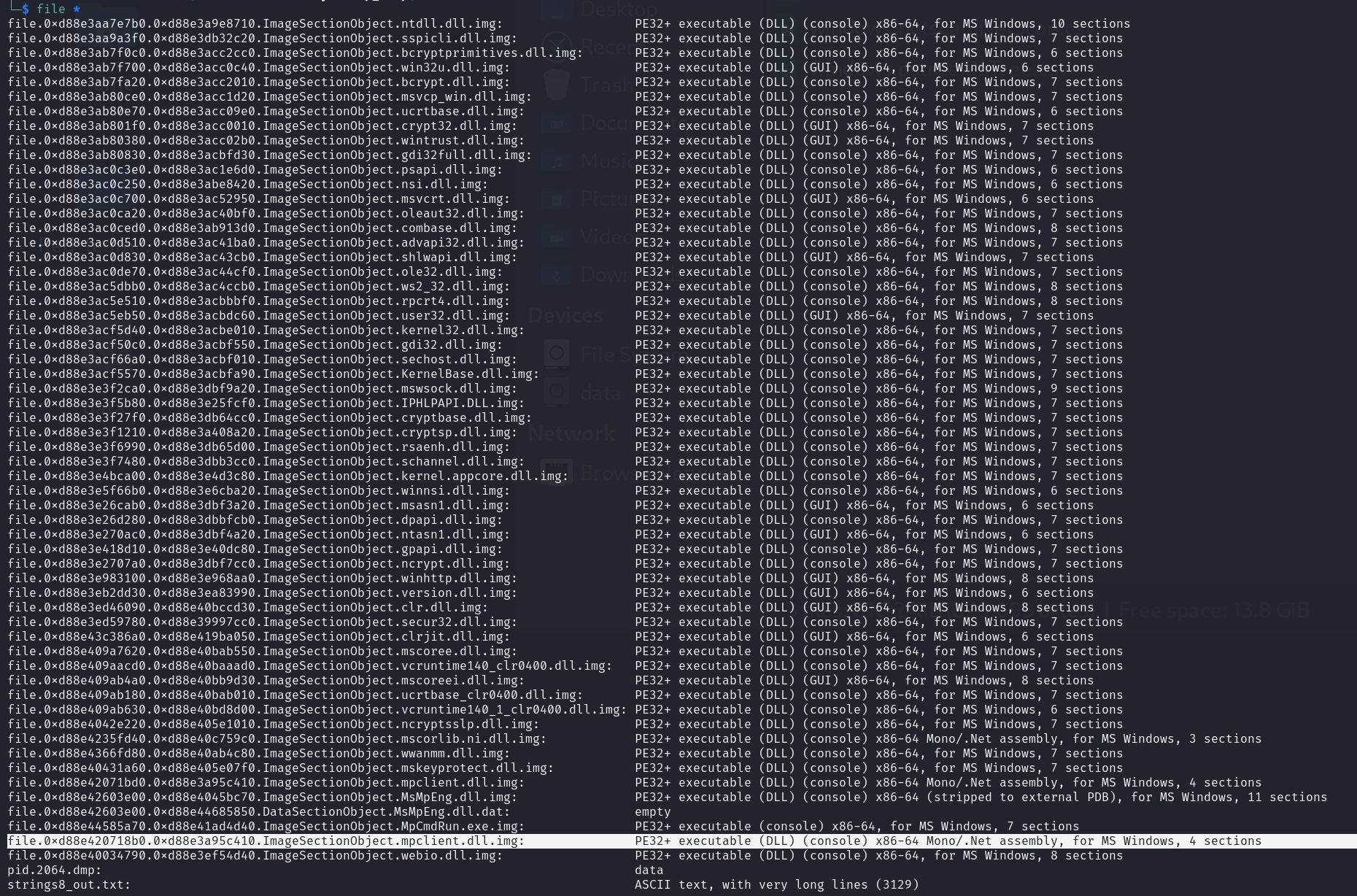
3.2 Review all files
3.3 found interesting C# DLLs
3.4 Decompile C# DLL using ILSpy
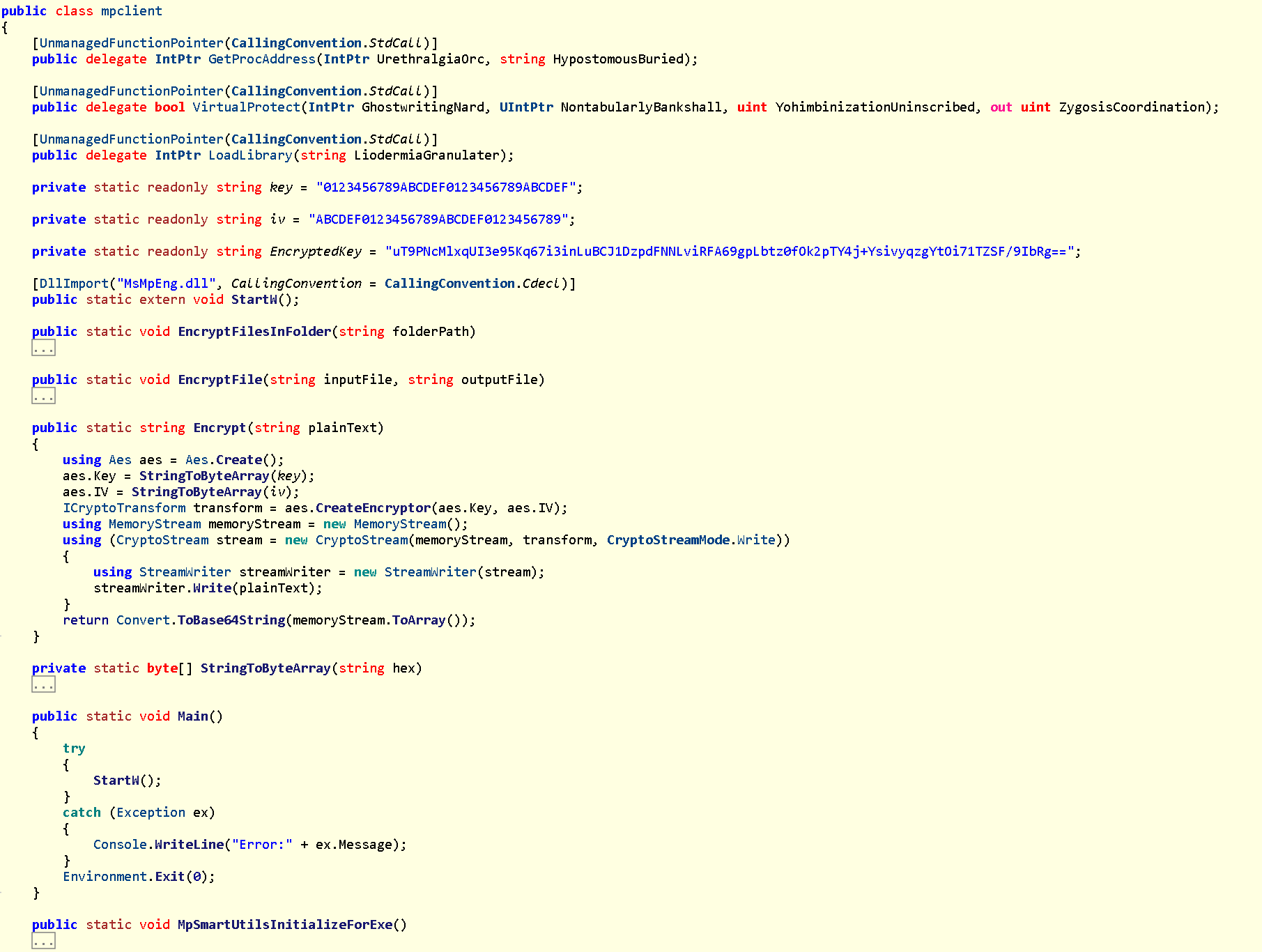
- The
EncryptedKeycontains the flag, but you need to usekeyandivto decrypt it. - The
Mainfunction will call the loadedMsMpEng.dllwithStartW()function which may contain the real C2 payload.
3.5 Decrypt the EncryptedKey
Here is the decypt program in C#:
1 | using System; |
Get the base64 encoded string.

3.6 Decode again and get the flag
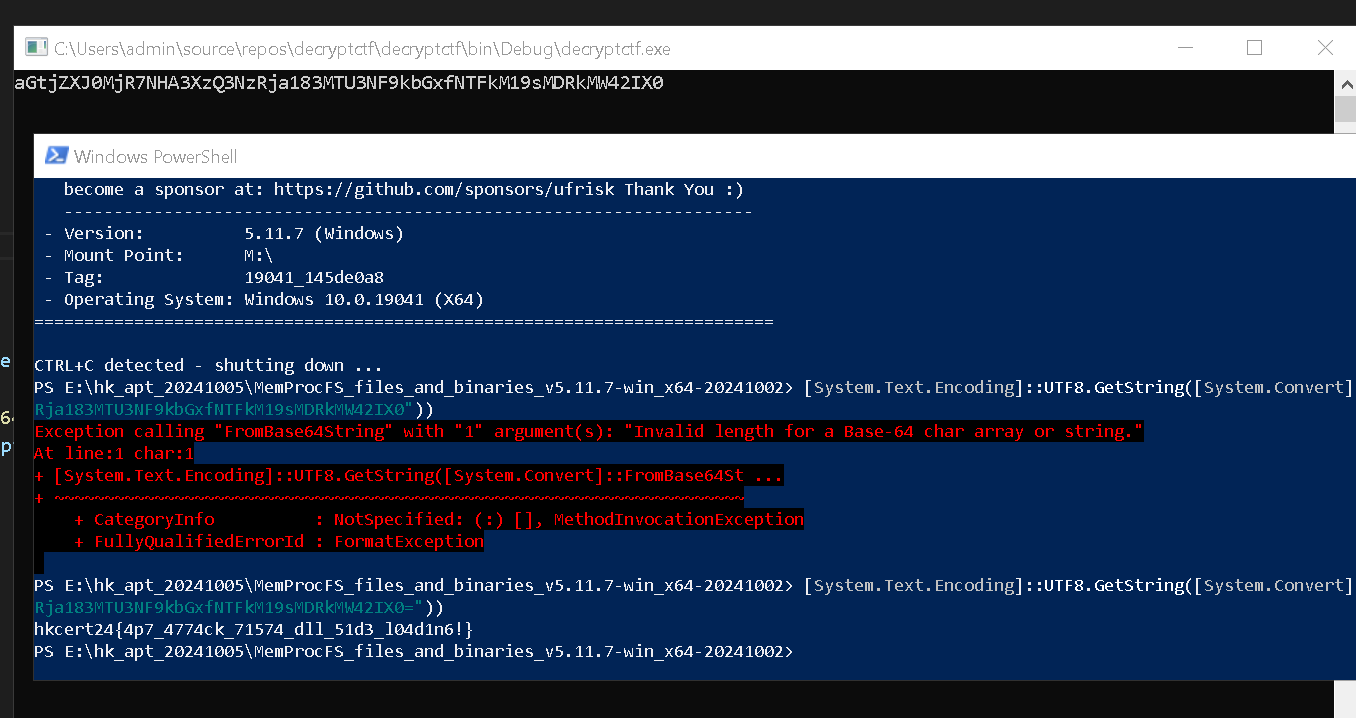
Flag
1 | hkcert24{4p7_4774ck_71574_dll_51d3_l04d1n6!} |
