HKCert CTF Forensic - Wheres the APT Attack 1 Guide
HKCert CTF Forensic - Q1: Where’s the APT Attack? APT攻擊在哪裡? Suspicious file 可疑檔案
Info
- Author: Nightsedge
- Categories: forensics
Question Description (zh-HK)
您是高級網絡安全分析師。
您的經理要求您協助分析Windows內存映像,作為我們目前調查的一部分。
這臺受害機器已經被隔離,Windows內存映像已經被提取供您調查。
預計內存映像將揭示一個包含命令和控制(C2)進程的常見程序,通常被稱為信標 (beacon)。
請找出常見有趣進程中可疑檔案中的旗。
Question Description (en)
You are the Senior Cybersecurity Analyst.
Your Manager is requesting your assistance in analyzing a Windows memory image as a component of our current investigation.
This victim machine has been isolated and the Windows memory image has been extracted for your review.
The memory image is expected to reveal a routine that includes a command and control (C2) process, commonly known as a beacon.
Please find the flag from the suspicious file from the common interesting process?!
Steps
- Open and analyze the memory image by using Volatility3 and MemProcFS
- Identify the interesting file and get the flag from the process dump
Warning
- Real Malware
- Can bypass Anti-Virus Solutions
- Almost no signature? maybe not?
- Not useful: malfind (because no signature), yarascan (or you have your own great Yara signature)
- The author (me) is too lazy to tidy up the write-ups~
GonJK provided a detailed step-by-step guide for this challenge for this competition, please give him respect with thanks
HKCERT CTF 2024: Guide to beginner-friendly challenges
Guide
From the title of the question, already told that it is an APT Attack, APT means “Advanced persistent threat”.
Therefore, if you understand this term, you can start by looking for persistent tactics on Windows OS.
There is a good reference from MITRE ATT&CK framework.
1. Basic Analysis to understand the memory image environment
1.1 Using Volatility3 commands to understand the memory image first
1 | vol.py -f hk_oct_apt_attack.mem windows.info.Info |
1.2 Using MemProcFS (Windows) to mount as a drive and understand the memory image first (Please refer to GonJK step by step guide)
1 | .\MemProcFS.exe -device .\hk_oct_apt_attack.mem -forensic 1 -v |
1.3 Volatility3 result to CSV
Why CSV? Maybe it is easier to co-relate the records and/or create a timeline in excel.
1 | vol.py -r csv -f /home/kali/Downloads/hk_oct_apt_attack.mem windows.netscan.NetScan > ./review_records/windows.netscan.NetScan.csv |
2. Identify the interesting file
2.1. Way 1 - Using the FileScan function to find the interesting file
1 | python3 vol.py -r csv -f /home/kali/Downloads/hk_oct_apt_attack.mem windows.filescan.FileScan > ./review_records/windows.filescan.FileScan.csv |
You can go through all files, and there is a .bat inside the user(night01)’s Startup Folder AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup.

Dump it for analysis.
1 | python3 vol.py -f /home/kali/Downloads/hk_oct_apt_attack.mem -o ./dump_temp/ windows.dumpfiles.DumpFiles --virtaddr 0xd88e43c80bd0 |
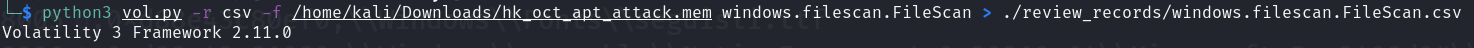
Failed to dump. sometimes like that, maybe the cache is corrupted or the MFT table is wrong.
You can try to fix this, but it will be hard to recover.
Suggested to use MemProcFS to find it directly. Because MemProcFS already helped to fix this problem.M:\forensic\ntfs\1\Users\night01\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Windows_Update_kb4781465.bat
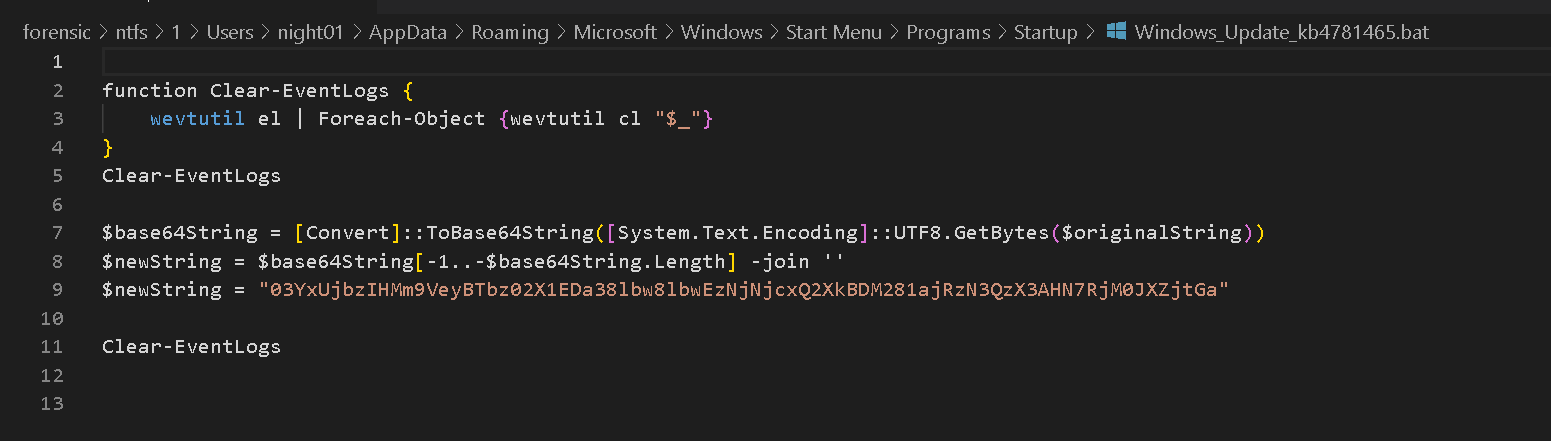
Way 2 - 2.2 Investigate the powershell process
The cmd.exe and powershell.exe are the interesting processes as always.
We can dump the powershell process (PID: 2064). and grep strings with $ because powershell script defines variables using $.
1 | python3 vol.py -f /home/kali/Downloads/hk_oct_apt_attack.mem -o ./dump_temp/ windows.memmap.Memmap --pid 2064 --dump |
if MemProcFS, check the minidump folder of the process.
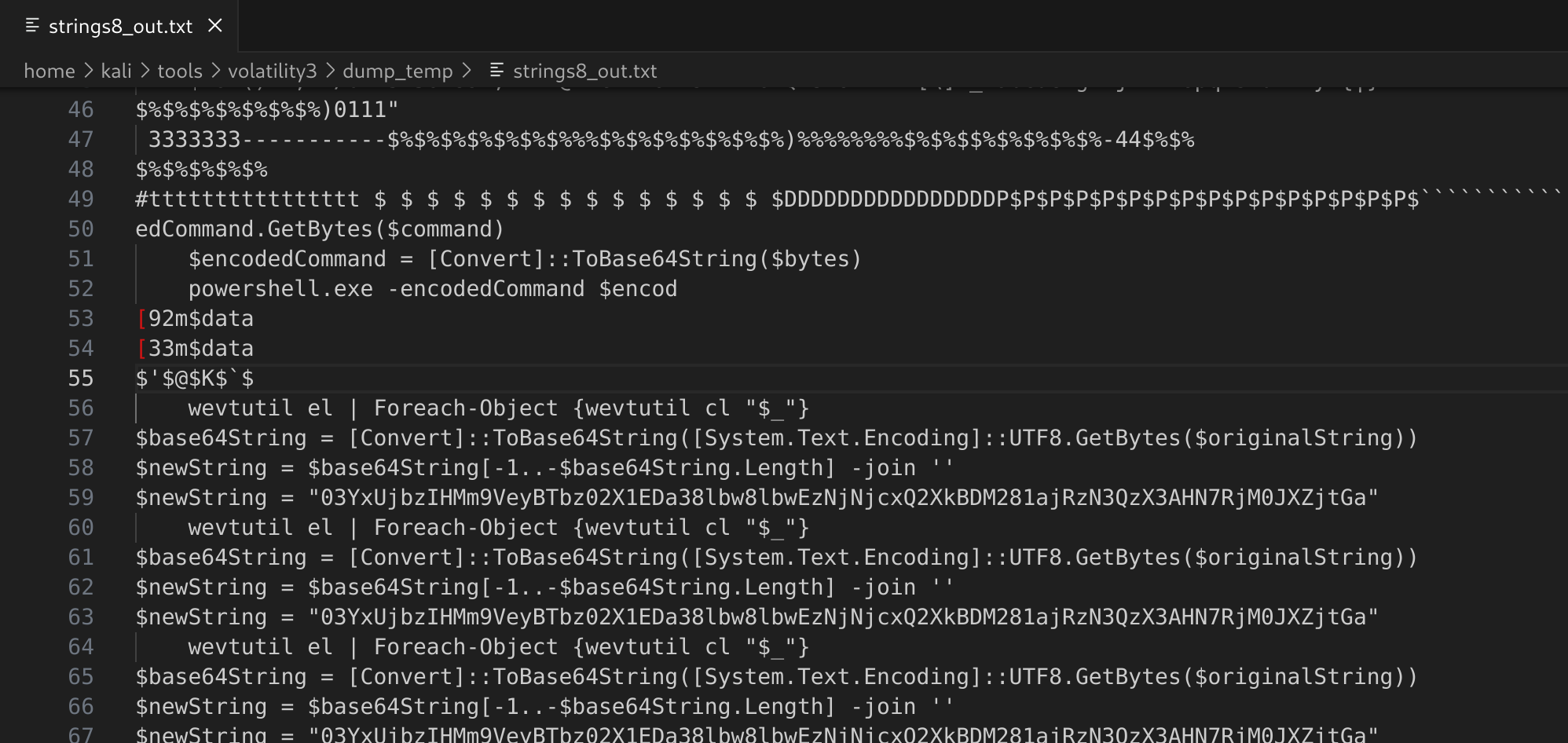
Now, The string output contains some interesting powershell commands:
wevtutil el...$base64String...$newString...
Back to the dump file and check those keywords again. You will find the following script.

The script contains the following steps:
- clear the event logs
- Base64 string
- Reverse string
And the “Write-Host” command contains the flag but you need to reverse the string and base64 decode it.
Here is the flag.
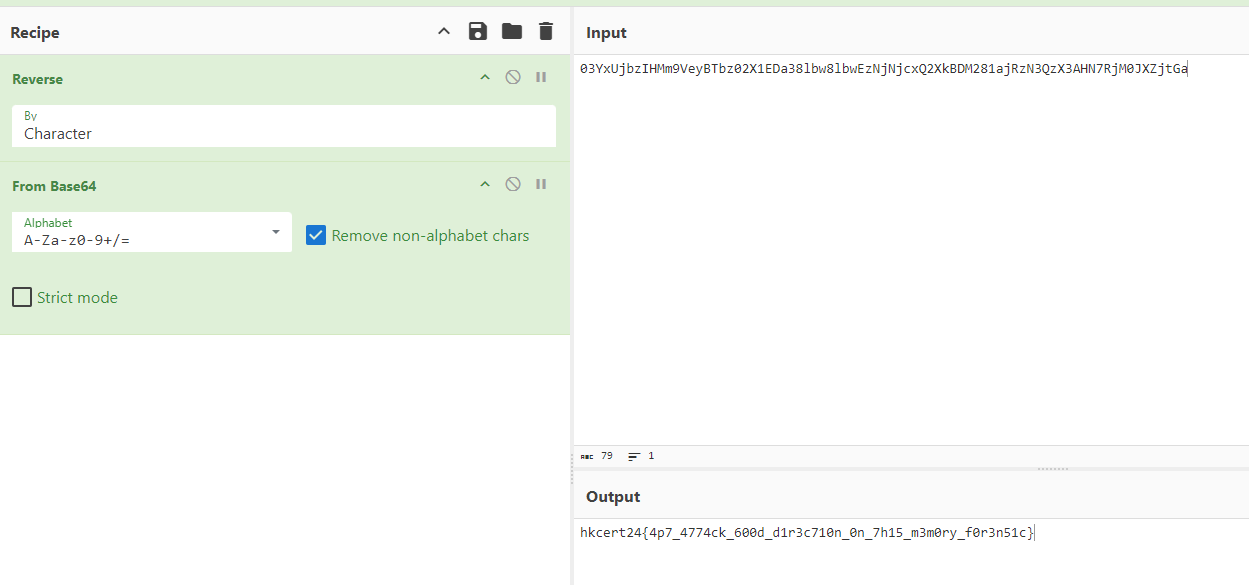
Flag
1 | hkcert24{4p7_4774ck_600d_d1r3c710n_0n_7h15_m3m0ry_f0r3n51c} |
Hint for next question: from this flag “APT attack good direction on this memory forensic”
What’s the meaning of this hint?
First of all, the bat file is place in Users\night01\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup which is a typical persistence method.
T1547.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder
Please refer to the following URL link and read more about this technique:
https://attack.mitre.org/techniques/T1547/001/
